Are you looking for a way to automatically detect what network you’re on when using Global Secure Access? If so, this post is for you.
In my recent evaluation of Global Secure Access (Entra Private Access), I encountered a key challenge that I suspect many of you might be facing. Despite the “intelligent local access” feature being enabled, network traffic was unexpectedly being routed through the Global Secure Access client when devices were on the corporate network. This defeats the purpose of intelligent local access and can impact performance and efficiency.
Seeking a solution, I discovered a valuable blog post by Morten Knudsen (Morten’s blog ). In his post, Morten effectively addresses this issue using Intune remediation techniques (which leverage Intune’s powerful built-in features to automatically detect and fix issues on managed devices).
While Morten’s approach is insightful, it didn’t completely align with my specific requirements, which necessitated focusing on external IP address detection to accurately determine if the device was truly on the corporate network. Inspired by Morten’s scripts, I developed my own solution, retaining the same fundamental approach to address the core traffic routing issue.
My version of the solution disables the Global Secure Access client by turning off the related services. This ensures that when a device is on the corporate network (and detected as such via external IP), the Global Secure Access client is deactivated, allowing for true local access.
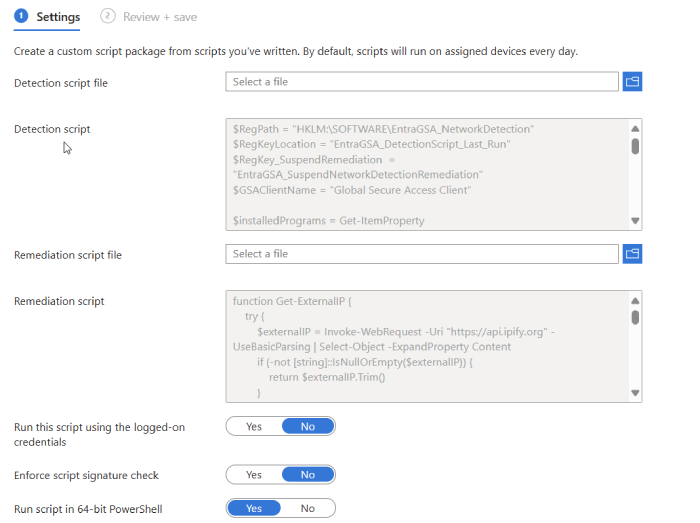
You can find my version of the remediation and detection script at Github .
I’ve assigned the remediation to run on all devices managed by Intune within our organization. Importantly, the detection logic ensures that the remediation (disabling the client services) will only run on devices that actually have the Global Secure Access Client installed and are incorrectly routing traffic on the corporate network. This targeted approach minimizes any unintended consequences.